A few day ago I had to investigate an email which contained a suspicious attachment. The attachment was a MS Office Word document using macros. The file is already in VT (d6fe6d4bffe60ea7bff109655426872bed44cbc3376249db7d9925a36b6e089c)
In this first post I am going to describe how it is possible to analyse MS Office files containing Macros. In further post I will describe how to perform malware analysis of the downloaded file, which it is an EXE file.
For the analysis, I will be using two main tools:
- oletools: included in Remnux v6.
- VBA debugger: included in MS office
'python-oletools is a package of python tools to analyze Microsoft OLE2 files (also called Structured Storage, Compound File Binary Format or Compound Document File Format), such as Microsoft Office documents or Outlook messages, mainly for malware analysis, forensics and debugging. It is based on my olefile parser' (source: http://www.decalage.info/python/oletools)
The Macros could also be dumped with oledump.py and some specific parameters. For example: oledump.py -s 7 -v suspicious.doc > Module1
However, in this case I am going to do the dynamic analysis through the MS Office debugger for VBA.
Debugging Macros
When opening the document in a sandbox there is an alert indicating the existence of Macros, which are not enable by default for security reasons:
Pressing ALT+F11 the debugger is open and clearly the Macros detected previously ThisDocument and Module1 are there:
The macro ThisDocument calls to a Function GetFolder which is inside the Module1 macro. This function is called once the file is open. GetFolder declares some interesting variables:
Now it it time to run the Macro. We can do it with F8 in order to debug it step by step. In the mean time, we can see the content of the variables (objects) in the Locals Window.
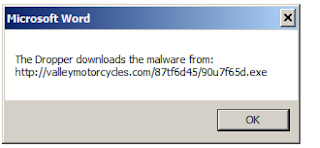
The function WarpChar is used to generated the URL where the malware is stored. So basically, this macro is acting as dropper. The URL where the malware is stored is http://valleymotorcycles.com/87tf6d45/90u7f65d.exe
We can see, through more debugging that the file download by the Dropper is kept as C:\Users\angel\AppData\Local\Temp\eccexlexb.exe
Later on, the file is executed through an 'open' function.
Modify Macros to display some debugging messages
Another alternative is to display debugging windows messages while the macro is being executed. For example, with the instruction "MsgBox".
Similar approach can be used to show where the dropper has been stored:
'MsgBox "The name of the stored file is: " & ShowSaveFil5'
Network traffic
While doing the analysis I captured the traffic in order to detect the network traffic generated and to be able to keep the malware file.
With this approach and set of tools I have been able to understand what the Macro embebed in an MS office document does. In this case it basically acts as dropper to download a file and execute it.
In following post I will reverse the malware downloaded